This article applies to customers that joined CoreView before May 2022. All new activations use our Secure By Default configuration, where Global Admin role is not required anymore.
This article will cover how to remove the global admin role from the CoreView admin account.
CoreView creates an administrative account in our customers’ Microsoft 365 accounts to act as the user that performs management activities within Microsoft. In other words, an operator will trigger a management action such as editing a user within CoreView, but the CoreView administrative account is the one that will perform the action within Microsoft. Historically, CoreView has required that this account be a Global Administrator to ensure it can perform any actions that might be needed.
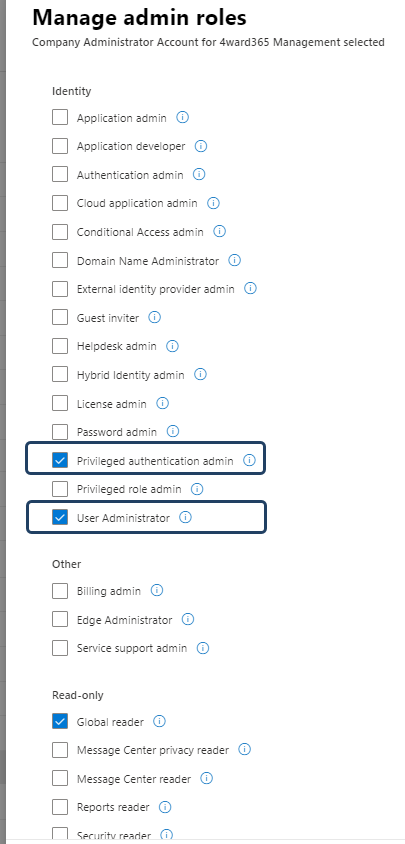
Given changes in security best practices, CoreView recognizes that dependence on a Global Administrative account can create undue risk. In our new Secure by default configuration, following roles are assigned to CoreView Admin account automatically:
- Global Reader
- Exchange Administrator
- Teams Administrator
- User Administrator
- Authentication Administrator
- SharePoint Administrator
For more information on roles, please refer to the “Assigning roles to the Graph application” article.
How to change permissions for existing admin accounts
For any existing CoreView customers, no changes will apply to your existing environment. If you would like to remove the Global Administrative role from your CoreView administrative account, you can perform the following steps.
Please close your advanced management session (if opened) and then you can assign the following permissions from section “Manage admin roles” of your Company Administrator user’s card from Microsoft 365 Admin Center:
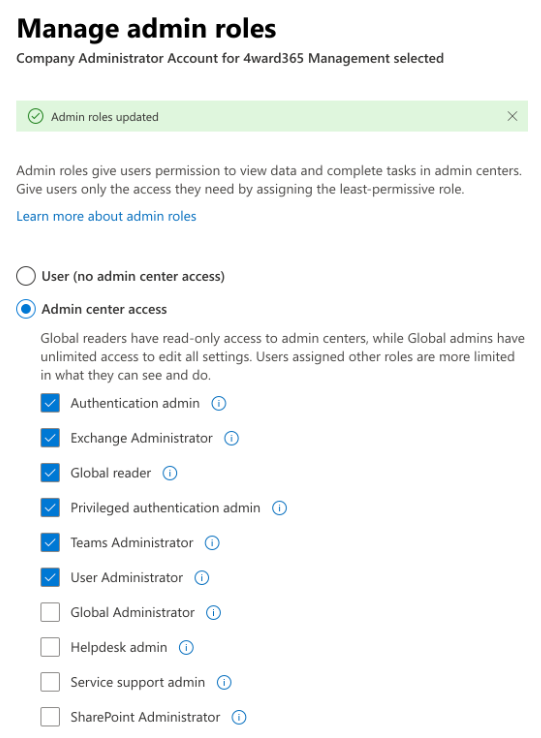
Please be sure to remove Global Administrator role from your list and assign the missing ones from the “Show all by category” section:
Click on the “Save Changes” blue button after you modified the permission assigned.
Password Rotation
Password rotation is achieved by adding the following Identity roles to the Graph application:
- Privileged Authentication Administrator
- Privileged Role Administrator
We have two rotation strategies in place:
For Advanced User Management
Password is automatically changed every 7 days and saved in CoreView Azure Key Vault - this is the password associated with the account named:
4ward365.admin@yourdomain.onmicrosoft.com For Service Account
Such as
coreview.reportsXY@yourdomain.onmicrosoft.comThe password is not changed by default, but it follows a long and complex pattern. The encryption key is rotated once per month and stored in CoreView Azure KeyVault. However, in the organization settings, it is possible to enable password changes for these service accounts if desired. For more information on how to do this, please refer to the article titled Settings in “Organization settings” under Security.
Please, note that the password is not changed unless settings to enable password rotation are used.
Re-enabling Global Admin privileges
If you want the CoreView application to be able to disable and manage passwords for Global Admins, you can add the Global Administrator role to the “company administrator” user.
FAQs
Do you change the password for “coreview.reports” accounts or only the encryption key? What is the password complexity?
For “coreview.reports” accounts, we encrypt the password and update the encryption key monthly. Additionally, users have the option to change their passwords via the portal. The required password complexity is 64 characters in length.
Do you change the password for “4ward365” accounts or only the encryption key? What is the password complexity?
For “4ward365” accounts, we update both the password and the encryption key. The password complexity requirement is 64 characters in length.
Can I manually change my 4ward365 password without giving Privileged Authentication Administrator and Privileged Role Administrator rights?
No, manual password changes are not possible because we need to regularly update the password and store it securely in our key vault.
Are the specified rights still necessary if enabled via Graph, as requested by the end of March 2024 due to Microsoft's deprecation?
Yes, these rights are still required because we are in the process of transitioning to Graph. The modules will remain in production for the next year. We continue to collaborate with Microsoft to address any regressions, poor performance, etc., so a complete switch to Graph is not yet feasible.
