Disabling MFA is essential for running CoreView properly with service accounts. However, to ensure the security of your tenant, it's crucial to use Conditional Access to block connections outside of our data center.
Requirement: You should have an Office 365 E1 license (or above). It is not necessary to have an Azure AD Premium P1 (or above) license.
Step 1
Login to Admin Office 365 portal
Step 2
In the navigation menu navigate to “Users” > “Active Users“

Step 3
Click on any active user. The user properties tab will appear on the right of your screen. Scroll down and click on “Manage multifactor authentication”.
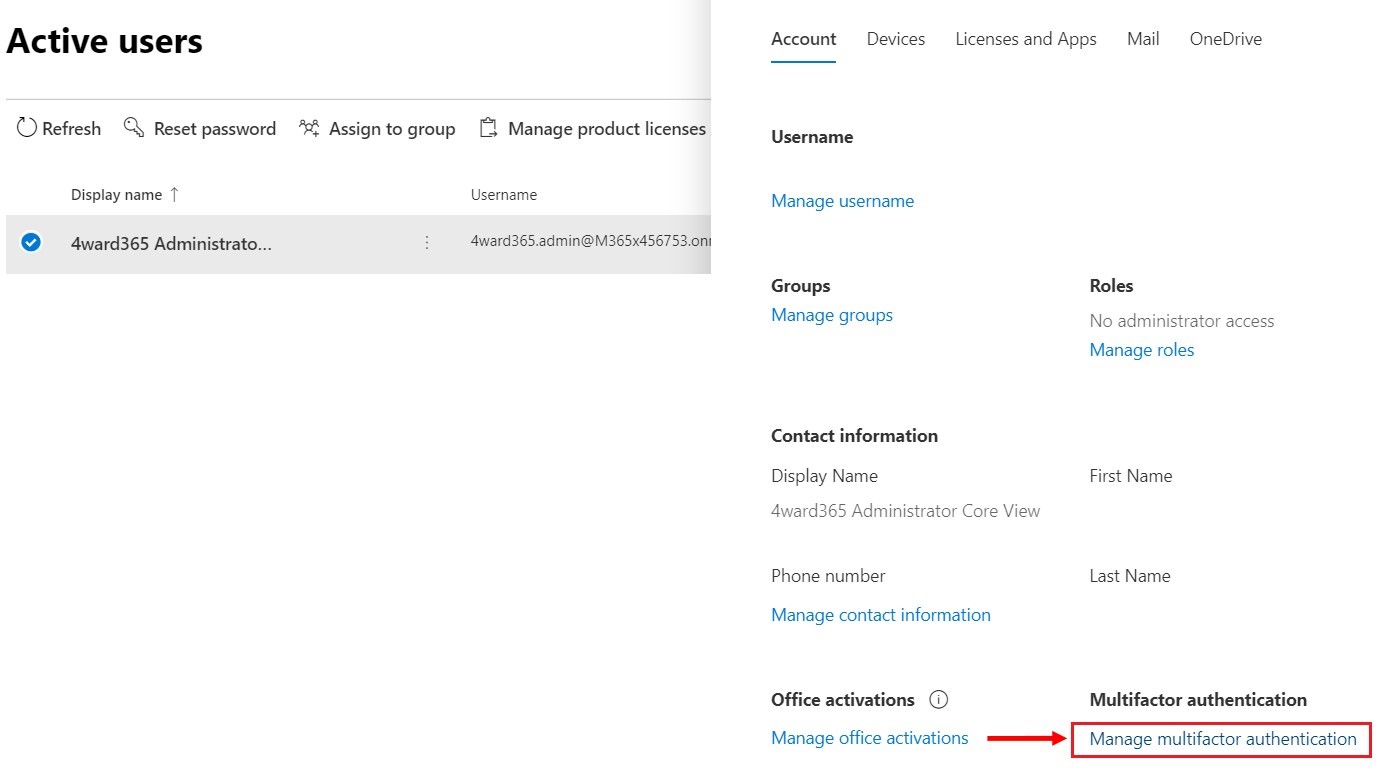
Step 4
Disable MFA for the CoreView Service Accounts. You should disable the Multifactor Authentication for the CoreView service users. To do that, click on the magnifying glass to open the search field.
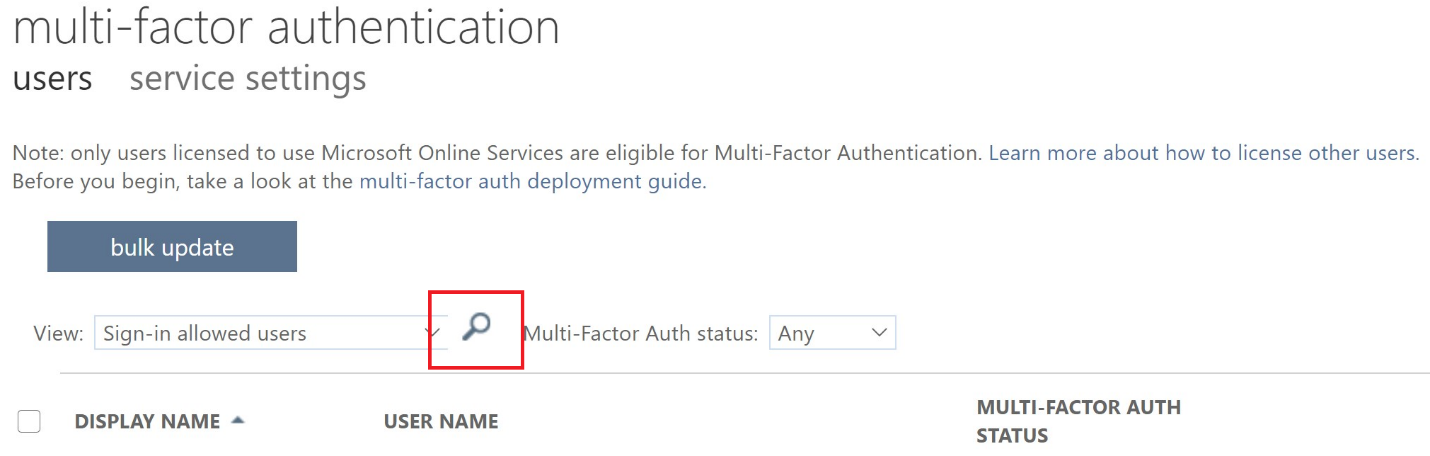
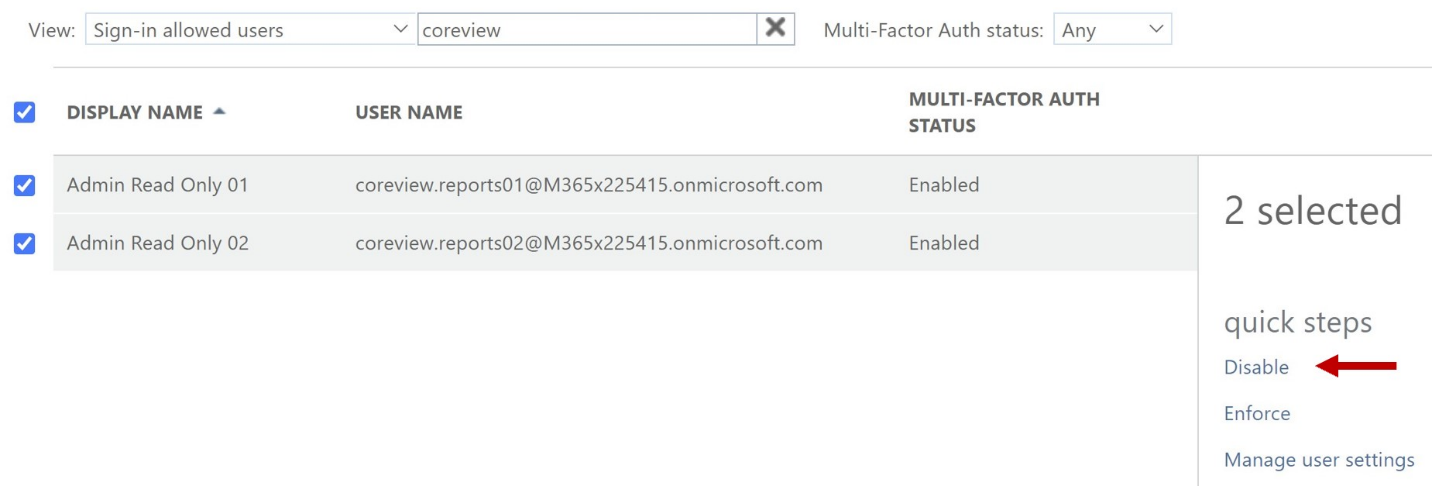
Search for and select all service users and click on “Enable” in the property menu.
Note: The number of service users depends on the size of your tenant.
If you require the naming rules for the service accounts, please consult your Technical Account Manager or reach out to Support.
If they already have the “Disabled” status, then you do not need to make any changes.
If the status is set to “Enabled”, then select the users that need to be disabled and click the “Disable“ option on the right side of the screen.
Another window will open, confirming your choice. Click "yes" to disable multi-factor authentication.

Close the confirmation window.

Now that MFA has been disabled for service accounts, it is crucial to ensure the security of your tenant by proceeding to the next step of the process. Please use Conditional Access to block connections from outside our data center.
Important note about Multi-Factor Authentication
If you have implemented Multi-Factor Authentication (MFA) for accessing your Microsoft 365 cloud services, please create a conditional access policy that prevents your on-premises Hybrid Connector IP address from asking for any second-factor authentication for the CoreView service account named
4ward365.admin@yourdomain.onmicrosoft.comWithout this exception policy, your CoreView tenant won't be able to open any management session.
Please be aware that your Hybrid Connector IP address may be behind a NAT applied by your network gateway for connecting to public networks such as the Internet. We recommend checking with your network specialist to identify your public IP address used by your on-premises for connecting to the public networks.
For more information about conditional access exception policy, please refer to the Official Microsoft documentation.
