The authentication method determines how Simeon authenticates into the tenant during a Sync in order to perform a backup, deploy changes, and any additional tasks.
Choose the authentication method
In addition to a Service Principal authentication, a user account is required, either through Delegated Authentication or Service Account Authentication.
Before proceeding…
If you haven't chosen the authentication method, read this article. It will highlight the importance of choosing the right authentication method and help you select the option that best fits your organization's security strategy, detailing the pros and cons of the different solutions.
Option 1: Delegated Authentication
With this option, Simeon authenticates into the tenant using an Entra ID user of your choice (usually a pre-existing Global Administrator in the tenant or a user with custom permissions).
- During the initial Sync, Simeon will ask you to sign in as this user. Simeon generates a refresh token for the user you authenticate with and then authenticates into the tenant using this refresh token.
- This method allows authentication with a user who is subject to MFA, Conditional Access, and other security policies.
- Should the refresh token become invalidated, you'll need to log into the Simeon app and re-authenticate to generate a new refresh token. The token can become invalidated for various reasons, such as changes in Conditional Access policies or sign-in policies, re-enrollment in MFA, or because of a short token expiration policy. It's important to note that these are examples and not an exhaustive list.
- Certain MFA enforcement types, like location-based enforcement, may not be compatible with delegated authentication unless using a self-hosted agent where the device location is under your control.
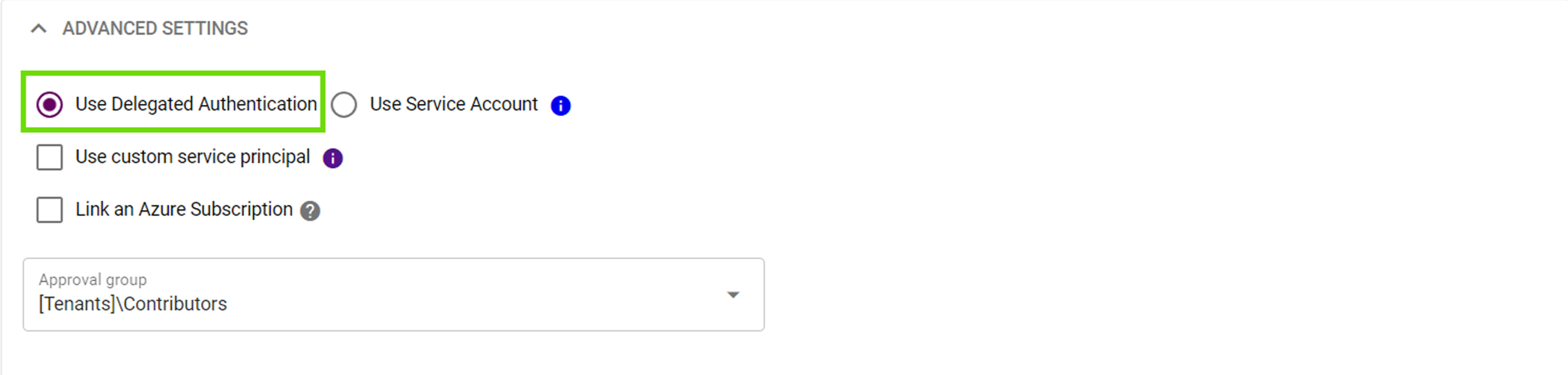
Option 2: Use Service Account
This option creates an Entra ID user named Microsoft 365 Management Service, with the UPN:
simeon@tenantdomainname in the tenant where you're installing.
Simeon then authenticates into the tenant as this user. Since no refresh token is used, changes to sign-in policies within the tenant generally won't affect the service account user's access.
- The service account user is assigned the Global Administrator role upon creation.
- Simeon generates a random 128-character password and securely stores it, along with the username, in an encrypted pipeline variable.
- You will need to exclude the service account from any Conditional Access policies that could limit Simeon's access to the tenant, including MFA policies.

