Playbook roles allow Tenant Admins to delegate responsibilities more precisely among their operators. There are three roles to view and manage Playbooks:
- Playbook Manager
- Playbook Admin
- Playbook Global Viewer
How to assign Playbook roles
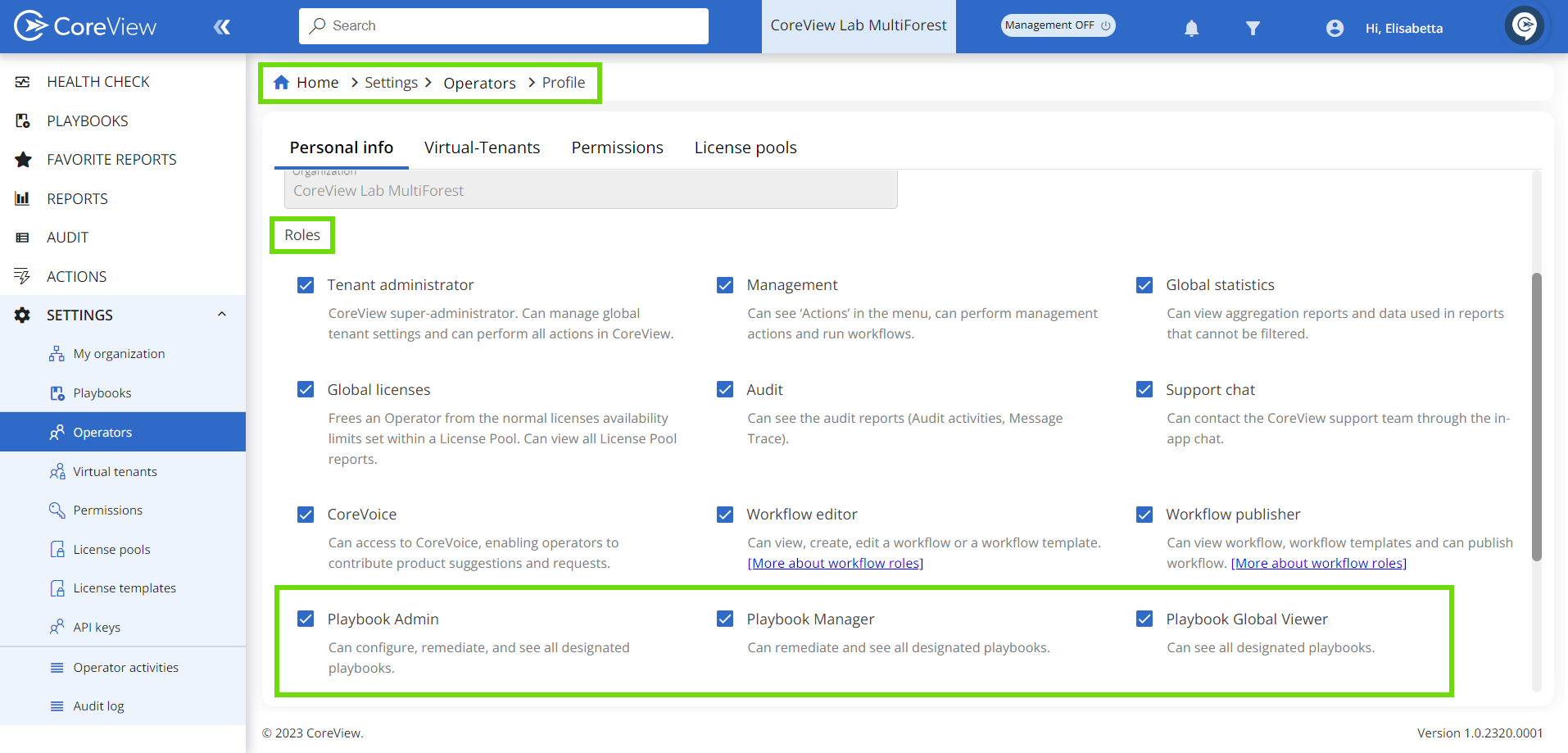
Tenant Admins can select the desired role in the operator's “Personal info” tab under “Settings”.
What can each Playbook role do?
Let's have a look at the differences between Playbook roles:
Tenant Admin |
Playbook Admin |
Playbook Manager |
Playbook Global Viewer |
|
|---|---|---|---|---|
| Create and edit custom policies | ✔️ |
✔️ |
|
|
| Edit Out-of-the-box policies | ✔️ |
|
|
|
| See designated Playbooks | ✔️ |
✔️ |
✔️ |
✔️ |
| Enable remediation | ✔️ |
✔️ |
|
|
| Run remediation | ✔️ |
✔️ |
✔️ |
|
| Schedule remediation (OOTB) | ✔️ |
|
|
|
| Schedule remediation (custom) | ✔️ |
✔️ |
||
| Set exceptions | ✔️ |
✔️ |
✔️ |
|
| See Strategic and Operational dashboards | ✔️ |
✔️ |
|
✔️ |
| See Monitoring dashboard | ✔️ |
✔️ |
✔️ |
✔️ |
| Customize (hide/show widgets in each Governance center tab) | ✔️ |
✔️ |
|
✔️ |
| Customize Governance center widgets* | ✔️ |
✔️ |
Overview tab |
✔️ |
*This refers to the ability to select which policies to display in the widget, the order in which they appear, and how to represent the matched items - either as a numeric value or a percentage.
It's important to note that while both Tenant Admins and Playbook Admins have similar capabilities, the actions of Playbook Admins are influenced by permissions.
How permissions affect Playbook roles
Permissions significantly influence the capabilities of each operator within the app. Each new Playbook role is subject to permissions, which can only be granted or revoked by a Tenant Admin. Let's examine the differences:
Tenant Admin
CAN |
CAN'T |
|---|---|
|
|
*Please note that only Tenant Admins can edit Out-of-the-box policies.
Playbook Admin
CAN |
CAN'T |
|
|---|---|---|
| Without permissions |
|
|
| With “Show all” permissions |
|
|
| With one or more Playbook permissions |
|
|
Playbook Admins can view all Playbooks unless specific permissions are assigned, which then restricts their view to only those Playbooks.
Playbook Manager and Playbook Global Viewer
Operators assigned the “Playbook Manager” or “Playbook Global Viewer” role will be able to see all Playbooks under the “Playbook” section in the menu, unless a Tenant Admin grants them specific Playbook permissions. Moreover, they won't have access to the Playbook Policy Library under “Settings > Playbooks”.
For more information on delegation, please visit the “Delegate Playbooks and policies” article.
Custom policy ownership restrictions
As mentioned above, both Tenant Admins and Playbook Admins can create custom policies. Let's examine in more detail what this ownership entails:
1. Tenant Admin creates a custom policy
When a Tenant Admin creates a custom policy, the following ownership restrictions will apply:
- Neither Playbook Admins nor Playbook Managers will have the ability to modify this policy.
Tenant Admin |
Playbook Admin with permissions |
Playbook Manager with permissions |
Playbook Global Viewer with permissions |
|
|---|---|---|---|---|
| View custom policy | ✔️ |
✔️ |
✔️ |
✔️ |
| Execute custom policy | ✔️ |
✔️ |
✔️ |
|
| Edit custom policy | ✔️ |
|
|
2. Playbook Admin creates a custom policy
If a Playbook Admin creates a custom policy, they can:
- Make it accessible to all Playbook operators with the corresponding permissions within their own V-Tenant, if applied.
- Permit Playbook Admins, and Playbook Managers to execute this policy remediation against matched items in the policy's V-Tenant (if any).
Tenant Admins will also be able to:
- View the policy
- Execute the policy remediation
- Disable the custom policy
- Delete custom policy
However, the following ownership restrictions will apply:
Tenant Admin |
Playbook Admin with permissions |
Playbook Manager with permissions |
Playbook Global Viewer with permissions |
|
|---|---|---|---|---|
| View custom policy | ✔️ |
✔️ |
✔️ |
✔️ |
| Execute custom policy | ✔️ |
✔️ |
✔️ |
|
| Disable custom policy | ✔️ |
|||
| Delete custom policy | ✔️ |
|||
| Edit custom policy | ✔️ |
Policy Box
The restrictions mentioned in this section will be reflected within the Policy Box: depending on the user's role and permissions, some actions will appear greyed out.
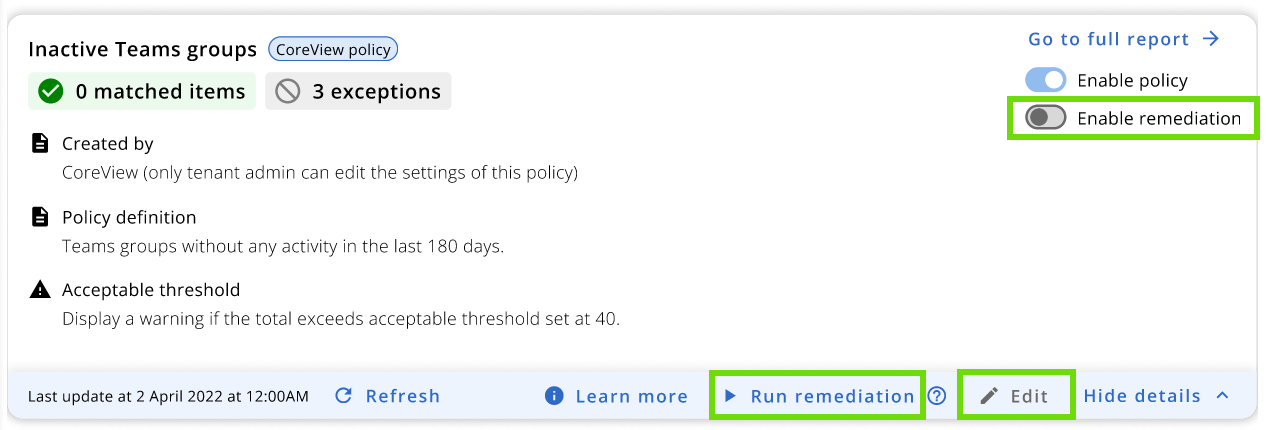
In the example below, a Playbook Admin looking at a custom policy created by another admin is not able to edit or delete the policy. However, the “Run remediation” button is enabled.
Created by
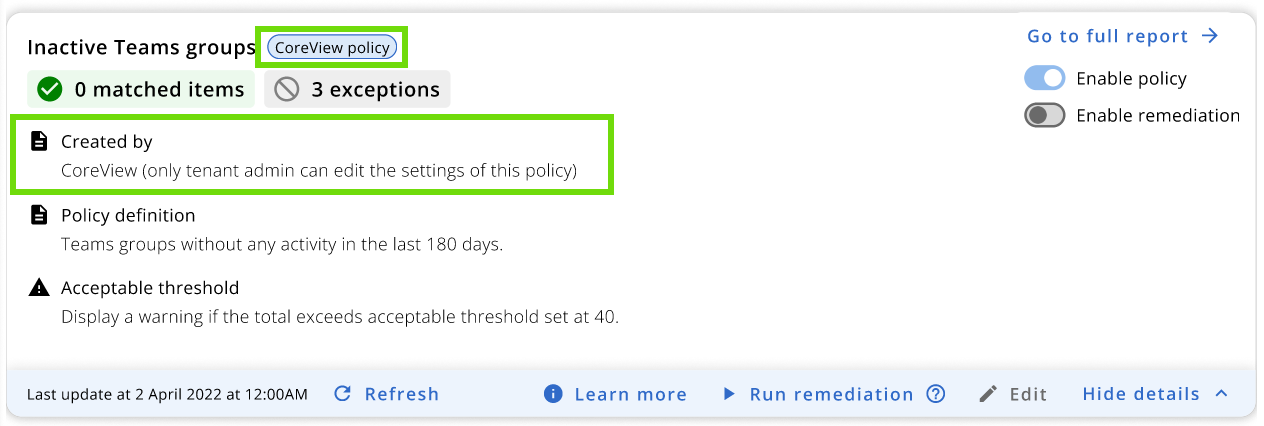
Within each Policy Box, the “Created by” section is visible to all operators who have permission to view the policy. Its purpose is to provide clear visibility regarding the policy's creator and help operators understand the associated permissions based on their roles.
When it comes to custom policies, the UserPrincipalName (UPN) of the policy creator will be displayed in this section. Out-of-the-box policies are shown as created by CoreView. For custom policies created by CoreView partners, the text “MSP” will be displayed instead of the UPN of the creator.