Here is a guide on how to apply best practice security recommendations for implementing the principle of least privilege in your environment.
The instructions provided are optional. You may adopt some, all, or none of the recommendations based on your specific needs and the sensitivity of your environment.
Hardening CoreView Hybrid Connector service accounts’ permissions (optional)
Below is a list of commands that management actions utilize within your hybrid environment:
Get-ADDomainController
Get-ADForest
Get-ADDomain
Get-Group
Get-ADGroup
New-ADGroup
Remove-ADGroup
Set-ADGroup
Set-ADAccountPassword
Get-DistributionGroup
Add-DistributionGroupMember
New-DistributionGroup
Remove-DistributionGroup
Remove-DistributionGroupMember
Set-DistributionGroup
Get-User
Get-ADUser
New-ADUser
Set-AdUser
Set-User
Get-Recipient
Get-RemoteMailbox
Enable-RemoteMailbox
Set-RemoteMailbox
Get-ADObject
Move-ADObject
Rename-ADObject
Set-ADObject
Unlock-ADAccount
Get-ExchangeServer
Get-ADRootDSEWe suggest granting your Active Directory service account delegated permissions on the Organizational Units you need to manage. This enables it to execute both the standard management actions available in the CoreView portal and any custom actions you create.
Using Active Directory Delegation only on specific Organizational Units, you can reduce the surface of attack. Additionaly, you can configure the security settings of PowerShell sessions, also referred to as PowerShell runspaces.
For additional details on Active Directory Delegation, please refer to the Microsoft documentation.
Active Directory Delegation
Instructions
Active Directory (AD) delegation allows specific users or groups to manage certain AD objects or attributes without full AD access. This grants more precise control over AD object management and is beneficial when different users or groups are responsible for various parts of the AD.
To delegate the necessary permissions to your Hybrid Connector service account, follow these steps:
- Open the Active Directory Users and Computers snap-in.
- Right-click the Organizational Units (OUs) you wish to delegate
- Assign the appropriate permissions to your service account.
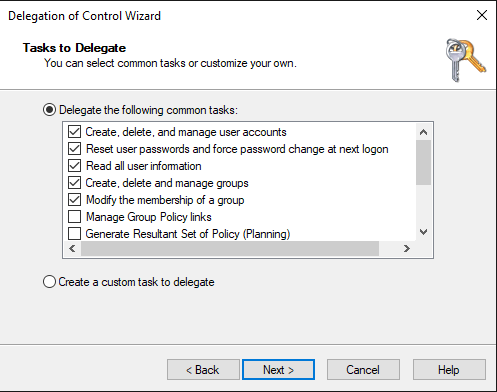
Ensure that you assign delegated permissions to each Organizational Unit (OU) in your Active Directory that you want to manage via the CoreView portal.
Remember to select the same OUs in the Organizational unit tree filter pane located in the On-Premises section of the “My organization” menu on the CoreView portal.
PowerShell remoting connection
Instructions
The CoreView Hybrid Connector utilizes your service account to execute commands and scripts on your Active Directory Domain Controller and Hybrid Exchange PowerShell virtual directory. It also accesses the PowerShell environment on these systems, enabling you to manage them remotely without executing individual logins through PowerShell remoting.
PowerShell remoting sessions are established using the “Invoke-Command” cmdlets.
PowerShell remoting lets you execute commands on remote computers via the PowerShell command-line interface (CLI). This functionality relies on Windows Remote Management (WinRM), which is Microsoft's implementation of the Web Services-Management (WSMan) protocol—a standard based on the Common Information Model (CIM).
For enhanced security, you can adjust your runspace configurations using the “Set-PSSessionConfiguration” cmdlet. This is especially useful for altering security settings within a PowerShell session configuration, like modifying which users or groups can connect.
We recommend creating a custom security group in your Active Directory environment and then adding the CoreView Hybrid Connector service account to that group.
After setting up the group, execute the following PowerShell script to configure the Microsoft.PowerShell session:
Set-PSSessionConfiguration microsoft.powerShell -ShowSecurityDescriptorUIAfter completing the setup, assign the “Execute (Invoke)” permission to your custom security group. This will enable your service account to remotely connect to your on-premises Domain Controller:
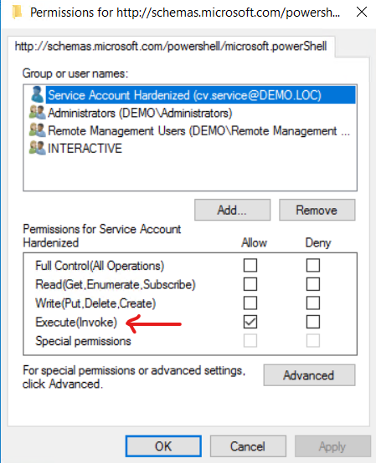
Ensure you execute this command on the Domain Controller that your hybrid agent server will be connecting to.
Exchange hybrid service account
Instructions
If your Hybrid Connector is tasked with managing the on-premises Exchange Server environment, ensure that your service account is granted membership in the Recipient Management group. For more information, please refer to the Microsoft documentation.
Functional limitations without On-premises Exchange
On-premises Exchange is NOT mandatory for Hybrid Connector operation. If no Exchange server is present, you can connect only Active Directory to the Hybrid Agent.
If no on-premises Exchange integration is configured, the following actions will not be available:
- Set custom attribute
- Add members to distribution groups (when the member is a mail contact)
- Remove members from distribution groups (when the member is a mail contact)
- Enable remote mailbox
- Create On-premises distribution group
- Edit mailbox
- Edit On-premises distribution group
- Remove On-premises distribution group
If you are using Exchange Online in a properly configured environment, mailbox-related actions can be performed via the “Mailbox” category.
If your distribution groups are managed in the cloud, use the available actions in the “Distribution Group” category.
Group Managed Service Account
Instructions
Be aware that a group Managed Service Account is not applicable in a Multi-Forest environment.
A Group Managed Service Account (gMSA) is a managed service account in Windows Active Directory that enables multiple computers to share a single account for service operations. It allows these computers to use a shared identity without requiring knowledge of the account's password, simplifying the management of service accounts across multiple machines.
The CoreView Hybrid Connector operates within a Docker instance that is not domain-joined. To enhance security via the Kerberos protocol, create a gMSA in your Active Directory specifically for the CoreView Docker container. For detailed information on gMSAs and containers, consult the Microsoft documentation.
The CoreView Hybrid Connector uses two separate Docker containers: one for management actions and another for importing objects from your on-premises environment. The container responsible for importing objects activates every 6 hours, follows the steps outlined in "CoreView Hybrid Connector - How On-Premises Import Process Works," imports objects, and then shuts down independently of the container that performs management actions.
To avoid Kerberos authentication conflicts when both containers are active, consider creating two distinct gMSA accounts in Active Directory if you need to assign a gMSA to the container for importing data, in addition to the one for management actions.
After creating your gMSA accounts, configure them in the CoreView Hybrid Connector settings file by adding the following entries to:
“Forward365.Service.PowershellService.Agent.exe.config” located at:
C:\Program Files (x86)\CoreView AgentRemember to stop the CoreView Agent Windows Service before editing the config file.
For the Docker container running management actions, add and configure these keys in the “AppSettings” section:
<add key="gMSAEnabled" value="true" />
<add key="gMSAName" value="your_gMSA_accountname" />For the container handling object imports, add and configure these keys:
<add key="gMSAImporterEnabled" value="true" />
<add key="gMSAImporterName" value="your_second_gMSA_accountname" />If gMSA configuration is not required in your scenario, set the keys to "false" or retain the default keys in the config file:
<add key="gMSAEnabled" value="false" />
<add key="gMSAImporterEnabled" value="false" />Ensure you are using at least version 1.0.6 of the CoreView Hybrid Connector to support gMSA configuration.
You can now restart the CoreView Agent Windows Service to apply the new configuration.
