By using the “What If” tool you can easily identify any policy that is currently blocking access to our service accounts:
coreview.reports<randomicnumber>@<onmicrosoft domain>or our management user:
4ward365.admin@<onmicrosoft domain>You can find the What If tool on the “Conditional Access - Policies” page in the Entra portal.
How to use the What If tool:
Step 1
To start the tool, in the toolbar on top of the list of policies, click “What If”.
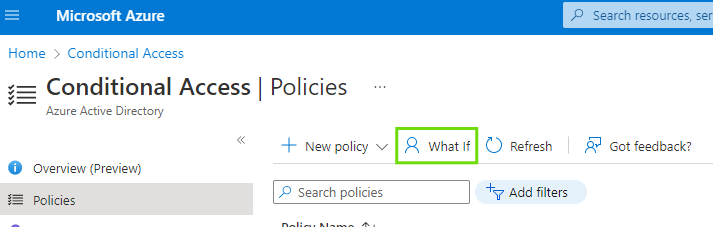
Step 2
In the User field type, expand the user or workload identity section, select User, and select from the list one of our accounts (i.e. coreview.reports<randomicnumber>@<onmicrosoft domain>):
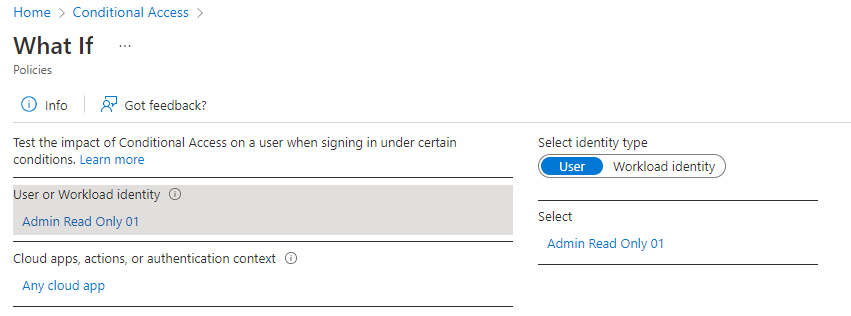
- In the IP address field: enter one of the addresses. Refer to the “List of IP addresses” for the IP addresses of each data center.
- In the location field: choose the information appropriate for your location
| For the… | Choose… | IP addresses |
|---|---|---|
| Europe Data center | Ireland | Azure CCC (EU) |
| USA Data center | Virginia | Azure CCC (US East) |
| Canadian Data Center | Quebec City | Azure CCC (Canada East) |
| GOV Data center | Virginia | Azure CCC (US East) |
| Australian Data center | New South Wales | Azure AUS (Australia) |
List of IP addresses
Data centers and IPs
If you need the list of CoreView's data centers and related IPs, we can provide you with a detailed table.
You can request the table from your designated Technical Account Manager or by contacting support.
Click on “What If” button and let us know what the evaluation results are.

Understanding the Evaluation result
The “What If” tool simulates a user login under specific conditions (e.g., login location, apps being accessed). It evaluates Conditional Access policies for each login attempt: policies from which the user is excluded will be skipped, while all others will be assessed. The tool categorizes policies into “Policies that will apply”, indicating those evaluated during the login, and “Policies that will not apply”, indicating those that will be bypassed.
Based on the simulation performed, you should expect to see varying results, as explained below.
Simulating a login from an IP address outside of CoreView
Under “Policies that will apply”, we should find the Conditional Access policy to grant access only inside the CoreView data center with “Grant controls” set to “Block”.
Simulating a login from an IP address within our network
In this case, you should see the same policy placed under “Policies that will not apply”.
In both scenarios, the “Policies that will not apply” should include the customer's policy that mandates MFA for everyone, as our accounts are to be exempt from this policy.
For further details, consult the Microsoft documentation or contact your CoreView representative.
